Page 430 - Emerging Trends and Innovations in Web-Based Applications and Technologies
P. 430
International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
Figure Explanation: Threat Intelligence
Threat intelligence is one of the essential components of InfraGuard's real-time threat detection and automated response
capabilities. Threat Intelligence is actually the gathering, analysis, and publication of information on possible threats to critical
infrastructure.
A. Types of Threat Intelligence
InfraGuard uses the following types of threat intelligence:
1. Open-source Intelligence (OSINT): Information gathered from public sources using social media, forums, and websites.
2. Closed-Source Intelligence: Information gained from proprietary sources, including threat feeds and vulnerability
databases.
3. Human Intelligence (HUMINT): Information derived from human sources, such as threat actors and insiders.
4. Technical Intelligence: Information derived from technical sources, including network traffic and system logs.
B. Threat Intelligence Sources
InfraGuard aggregates threat intelligence gathered from a wide range of sources:
1. Threat feeds: Real time feeds of threats from trusted sources, including Threat Intelligence Platforms, and SIEM systems.
2. Vulnerability databases: Databases of known vulnerabilities include the National Vulnerability Database
3. SIEM Systems : Systems that aggregate and analyze information related to security from various sources.
4. Incident Response reports: Reports provided by incident response teams and researchers.
C. Threat Intelligence Analysis
Some of the threat intelligence analysis capabilities of InfraGuard are as follows:
1. Threat Modeling: Determining the likely threats and their behavior.
2. Anomaly Detection: This method identifies unusual patterns of behavior, which may denote a threat.
3. Predictive Analytics: Statistical models along with machine learning algorithms are used for prediction of potential threats.
4. Risk Scoring: Assigns a risk score to each threat by using its potential impact and likelihood.
D. Sharing of Threat Intelligence
InfraGuard allows sharing threat intelligence between the different stakeholders including:
1. Security Operations Centers (SOCs): Teams responsible for monitoring and responding to security incidents.
2. Incident Response Teams: Teams responsible for responding to security incidents.
3. Threat Intelligence Platforms: Platforms that aggregate and analyze threat intelligence from various sources.
4. Security Information and Event Management (SIEM) Systems: Systems that collect and analyze security-related data from
various sources.
V. PERFORMANCE EVALUATION
Performance Evaluation Metrics
The following metrics are used in the paper to evaluate InfraGuard's performance:
Detection Accuracy: Real-time accuracy with which the system detects threats.
Response Time: The system takes to respond to the identified threats.
False Positive Rate: The rate at which the system generates false alarms.
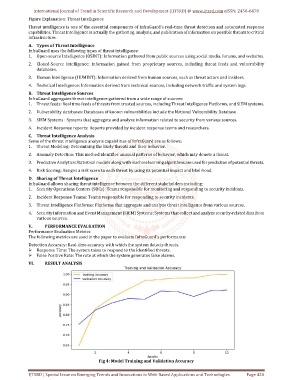
VI. RESULT ANALYSIS
Fig 4: Model Training and Validation Accuracy
IJTSRD | Special Issue on Emerging Trends and Innovations in Web-Based Applications and Technologies Page 420