Page 433 - Emerging Trends and Innovations in Web-Based Applications and Technologies
P. 433
International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470
IV. The Role of Real-Time Threat Detection in Critical Infrastructure Security
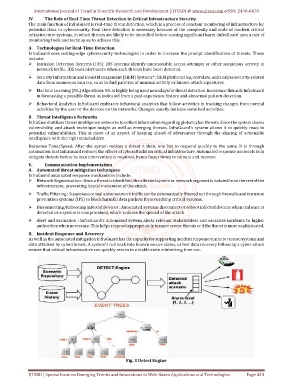
The main function of InfraGuard is real-time threat detection, which is a process of constant monitoring of infrastructure for
potential risks to cybersecurity. Real-time detection is necessary because of the complexity and scale of modern critical
infrastructure systems, in which threats are likely to be identified before causing significant harm. InfraGuard uses a mix of
monitoring tools and techniques to achieve this.
A. Technologies for Real-Time Detection
InfraGuard uses cutting-edge cybersecurity technologies in order to increase the prompt identification of threats. These
include:
Intrusion Detection Systems (IDS): IDS systems identify questionable access attempts or other suspicious activity in
network traffic. IDS tools alert users when such threats have been detected.
Security Information and Event Management (SIEM) Systems*: SIEM platforms log, correlate, and analyze security-related
data from numerous sources, so as to find patterns of unusual activity or known attack signatures.
Machine Learning (ML) Algorithms: ML is highly being used nowadays for threat detection. In essence, this aids InfraGuard
in forecasting a possible threat as indicated from a past experience history and abnormal pattern detection.
Behavioral Analytics InfraGuard embraces behavioral analytics that follow activities in tracking changes from normal
activities by the user or the devices on the networks. Changes usually indicate some bad activities.
B. Threat Intelligence Networks
InfraGuard utilizes threat intelligence networks to collect information regarding global cyber threats. Since the system shares
vulnerability and attack technique insight as well as emerging threats, InfraGuard's system allows it to quickly react to
potential vulnerabilities. This is more of an aspect of keeping ahead of adversaries through the sharing of actionable
intelligence with the right stakeholders.
Response Time/Speed: After the system notices a threat it then; one has to respond quickly to the same. It is through
automation that InfraGuard reduces the effects of cyberattacks on critical infrastructure. Automated response protocols help
mitigate threats before human intervention is required, hence faster times to contain and recover.
V. Communication Implementation
A. Automated threat mitigation techniques
InfraGuard automated response mechanisms include:
Network Segmentation : Once a threat is identified, the affected system or network segment is isolated from the rest of the
infrastructure, preventing lateral movement of the attack.
Traffic Filtering : Suspicious or malicious network traffic can be automatically filtered out through firewalls and intrusion
prevention systems (IPS) to block harmful data packets from reaching critical systems.
Disconnecting/Rebooting Infected Devices : Automated systems disconnect or reboot infected devices when malware is
detected or a system is compromised, which reduces the spread of the attack.
Alert and Escalation : InfraGuard's automated system alerts relevant stakeholders and escalates incidents to higher
authorities when necessary. This helps respond appropriately to more severe threats or if the threat is more sophisticated.
B. Incident Response and Recovery
As well as the automated mitigation InfraGuard has the capacity for supporting incident response teams to restore systems and
data attacked by cyberthreats. A system's roll back into known secure states, or lost data recovery following a cyber attack
ensure that critical infrastructure can quickly return to a viable state minimizing time out.
Fig. 3 Detect Engine
IJTSRD | Special Issue on Emerging Trends and Innovations in Web-Based Applications and Technologies Page 423